Disclaimer: Do not go about doubting technology after reading this article. We at Cyber Scribble are proponents and fans of technology. Our aim is to create awareness about 'technological abuse and dangers.' We humbly remind everyone that technology has given many benefits to humanity. Let's not forget that!
Good day to you all! Today we are going to start with one of our favorite excerpts from the Abrahamic scriptures.
What is mankind that you are mindful of them,
a son of man that you care for him?
You made him a little lower than the angels;
you crowned him with glory and honor and put everything under his feet.
Reading the above gives us a sense of pride and the feeling that mankind is amazing! Isn’t it? While we rejoice in our glory and awesomeness, it is also time to do justice to this post's title. Let’s begin.
Battle Tactics 1: Troy
Greeks laid siege to Troy for ten years primarily to retrieve Helen, the wife of the Greek king Menelaus, who was taken by Paris, the Trojan prince, sparking the Trojan War. One of the military advantages that Troy had at that time was their impregnable walls.
Troy was able to sustain the siege because of its massive wall, which was ahead of its time. It is believed that Troy had ample supplies of food and water within the city, possibly from springs and local food production, allowing life to continue normally without any disruptions.
Finding the Weakness , Breaking the Defense
Odysseus, a military strategist who observed the Greeks for ten years on the battlefront, understood the following simple truths or weaknesses about the enemy
Overconfidence (For 10 years, they could not break us)
Sole reliance on unbreakable wall (Made by the gods)
Reliance on their divine favor (The gods love us)
Desire for victory
A determined foe finds a way
Odysseus, as any determined enemy , devised a brilliant plan to exploit every weakness mentioned above.
He proposed sending a large wooden horse as a gift and offering and as a symbol of the “Greeks accepting defeat”. It worked because it appealed to Trojans,
Desire for victory
Divine nature ( Deities do accept offerings :-p )
Confidence
It also enabled maneuvering past their defensive walls with ease by hiding soldiers inside the horse.
Outcome
Troy accepted the offering and took the horse inside their defensive walls, celebrating the entire night with victory dances and drinks. This allowed the Greeks to break the wall defenses and defeat Troy.
Battle Tactics 2: The 'Perfect Battle' at Chancellorsville
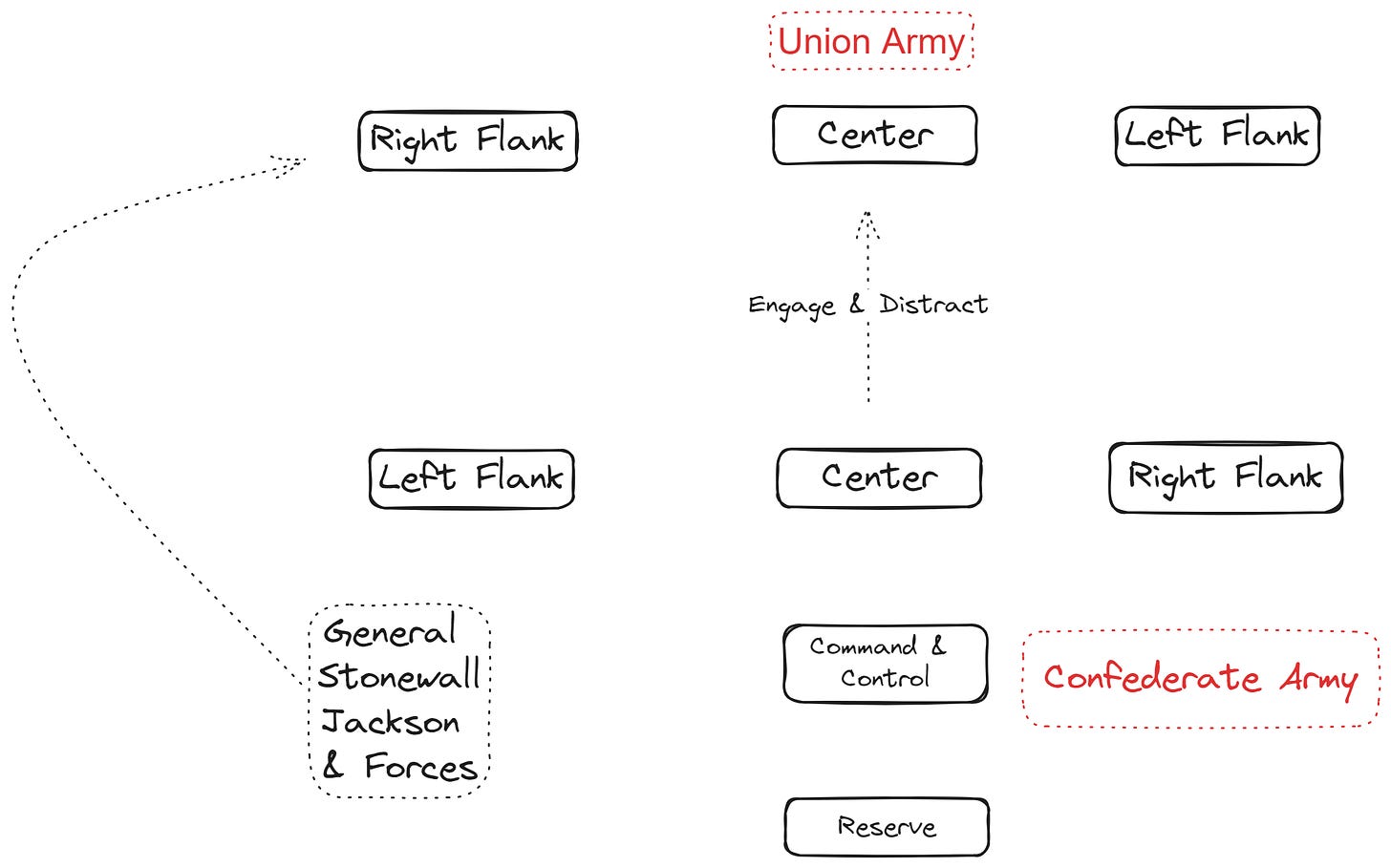
In the Battle of Chancellorsville, Confederate General Robert E. Lee faced a major hurdle: he was significantly outnumbered by Union forces under General Joseph Hooker.
A Bold Risky Strategy
Determined to win, Lee executed a bold and risky strategy. He divided his already outnumbered army, sending a large portion under General Stonewall Jackson on a flanking march around the Union army’s right flank. To add icing on the cake, he maintained a smaller force in front of the Union army at Chancellorsville to engage and distract them.
Unfortunately, Hooker fell for this strategy. Convinced that Chancellorsville was the main Confederate effort, he focused all his attention and resources there, neglecting to scout his flanks adequately.
Outcome
This oversight and carelessness allowed Jackson’s forces to complete their flanking maneuver unopposed. When Jackson's troops attacked the unsuspecting Union right flank, it caused chaos and panic, collapsing multiple Union defense lines that had been weakened by the concentration of resources on the front.
This strategic diversion by Lee, making it appear that the primary threat was directly in front while a more dangerous threat was building on the flank, is a prime example of shifting an opponent’s focus to exploit weaknesses in their defense lines.
Defense Of Humanity
Here is another one of our favorite lines from the Abrahamic scriptures.
God created mankind in his own image, in the image of God he created them
How cool is that!
On the surface, Humanity defends itself through a sophisticated system of defenses.
Collectively
We are located in the far corner of the universe, alone and well protected by the void (it takes light years to reach us).
We are massive in size (last we checked, 8 billion of us here and we are still growing).
Individually, our bodies have well-defined defenses at macro level
Ears perceive auditory dangers.
Eyes detect visual threats.
The nose senses harmful odors.
The brain processes these signals.
Limbs initiate protective responses like reflexes, fight-or-flight reactions, and strategic attack planning to ensure survival.
Many more!
The Hypothetical Siege On Humanity
Now, let's embark on an imaginative journey to explore a hypothetical scenario where an unseen enemy faces the challenges of breaking through humanity's defenses. How might such an adversary overcome these obstacles? Let's delve into this hypothetical scenario.
Breaking the Wall of Void
Physically, we are well protected by a void of vast empty space. For an enemy to reach us from a nearby star system, it would take a minimum of 4.24 light years. What a marvelous design to protect one’s children, isn’t it?
Yet, there are weaknesses in the design: we are reachable by following for a distant enemy
Darkness
Light
Thought
??
Let’s assume the enemy decides to use ‘Thought’ as the horse to break into our defenses, how would such an enemy would do so ?
Breaking the ‘Size Advantage’ : Winning the First Battle!
Through thought enemy would do the following;
Divide us into Race
Divide us into Language
Divide us into Religion
Divide us into Countries
Divide us into many other forms by simply using ‘Thought’
By such divisions , the enemy is able to keep us at odds and busy with problems among ourselves shifting our focus and energy totally internally!.
Breaking Individuals : Winning the Next Battle!
A determined hypothetical enemy will not stop at mere single battle victories. If the hypothetical enemy wants to win the war, they would need to defeat every individual guarding such a system. However, we are inherently well protected by design. If such an enemy wants to break us, then they have to:
Break our individual defensive protections at macro level
Ears
Eyes
Nose
Limbs
Brain
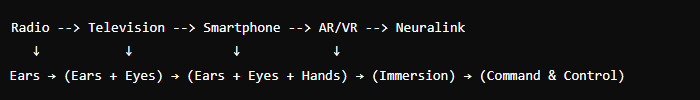
The hypothetical Enemy could gradually introduce the following to take our defenses and focus them on something else:
Radio: Saturate the ears with distracting or misleading information.
Television: Utilize visual and auditory stimulation to manipulate opinions and distract attention.
Smartphone: Create dependency on constant notifications and social media, diverting focus and our senses ( ears / eyes / hands ).
AR/VR: Immerse individuals in virtual environments, blurring the lines between reality and fiction.
Neuralink: Directly interface with the brain to control thoughts and behaviors. Take control of our Command & Control.
By gradually integrating these technologies, an enemy could shift focus away from critical awareness and weaken our natural defenses.
Also, this hypothetical enemy could top it up by enabling competition and scaling it globally at rapid speed through instant connectivity.
Alright! We are going to stop our imagination horse right here! and move on to most important thing we want to talk about!
Why This Blog ?
For those wondering, why such a horrible imagination ? We want to emphasize a crucial cyber hygiene through this blog which is,
Using Technology Wisely With Well Defined Boundaries and Practices!
and to remind each of us of the importance and strengths of our design. Hope it was entertaining to read!
Oh, by the way, did you all know that Cassandra and Laocoon warned the Trojans of deception regarding the horse? However, fueled by the desire for victory, their confidence in their superiority, and their belief in divine favor, they decided to bring the horse in anyway!
See you all on another weird post!
We are Secure By Design!
Weak by Desire!